The growing availability of low-cost computer chips and accessibility of high bandwidth communication have fueled an explosion of connected, intelligent devices. These devices can talk to the cloud and one another — a phenomenon known as the Internet of Things (IoT).
These devices have introduced new possibilities for mirroring the physical world within a digital landscape. They make it possible to control and track equipment and assets from one location and produce actionable insights to optimize operations. In short, they have driven forward-facing visions for industry and infrastructure that would have been considered science fiction not long ago.
Yet this rapid development has risks. As billions of devices have become connected through embedded IoT modules, security considerations have often taken a back seat. As a result, devices are more vulnerable to various cyberattacks. The impacts of these attacks reach far beyond the integrity of the devices alone.
System failures resulting in service outages or data breaches can lead to significant financial disruptions and lasting brand reputation damage. A report in Cybercrime Magazine reimagined the cost of cybercrime as a gross domestic product (GDP). The report even pegged it as the world’s third-largest economy, behind only the U.S. and China.
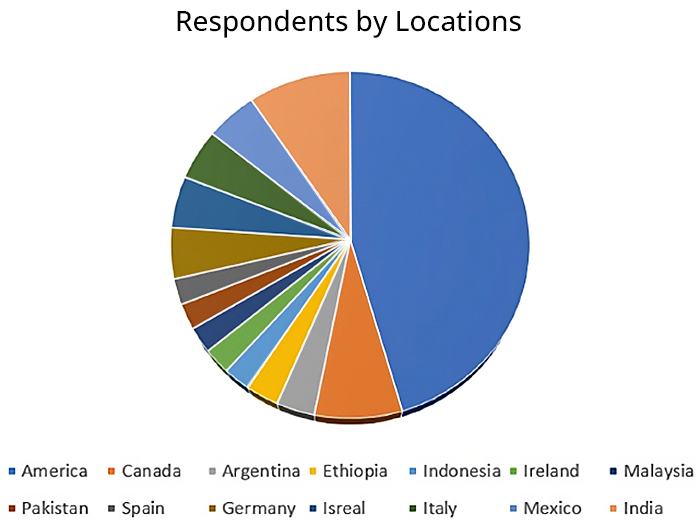
Figure 1: GlobalSpec’s survey was sent to hundreds of thousands of users worldwide, spanning multiple industries and job functions. (Source: GlobalSpec)
Table of Contents
Telit Cinterion and GlobalSpec
Telit and the cellular IoT business of Thales recently joined forces to become Telit Cinterion in 2023. This brought together decades of IoT know-how and Thales’s expertise in digital identity and security to help with these challenges.
To better understand the security issues facing organizations using IoT, Telit Cinterion partnered with technology services company GlobalSpec. GlobalSpec conducted a survey designed to gauge the needs of hundreds of users worldwide (shown in Figure 1) across industries, including:
- Industrial machinery, tools and equipment
- General manufacturing
- Oil and gas
- Packaging machinery
- Semiconductor and electronic components
- Transportation
- Utilities and energy
- Agriculture and forestry
- Building and construction
A Firsthand Look at Cybersecurity in IoT
The survey results offered a firsthand look at the growing concern felt by stakeholders throughout the IoT ecosystem. Many feel unprepared to handle cybersecurity threats. Only 10% of survey respondents indicated their organizations were ready to combat emerging and existing threats, as shown in Figure 2.
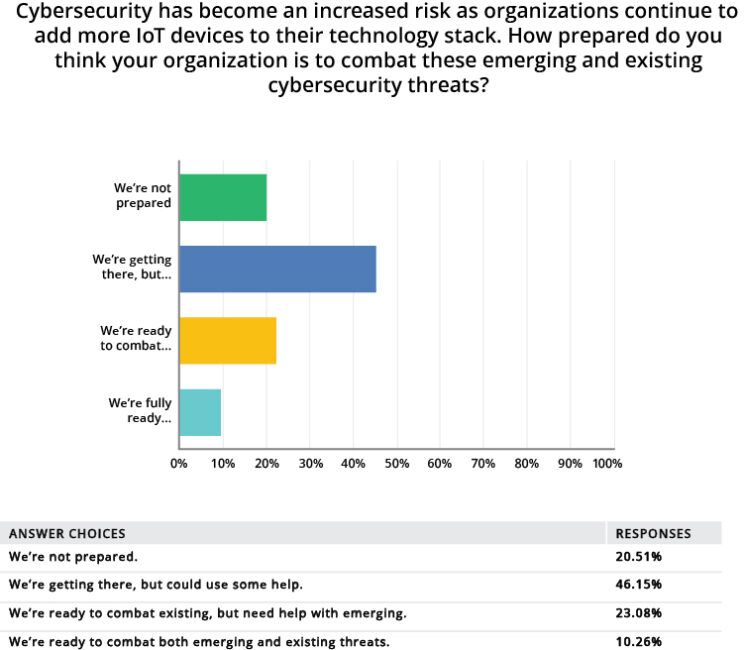
Figure 2: GlobalSpec’s survey was sent to hundreds of thousands of users worldwide, spanning multiple industries and job functions. (Source: GlobalSpec)
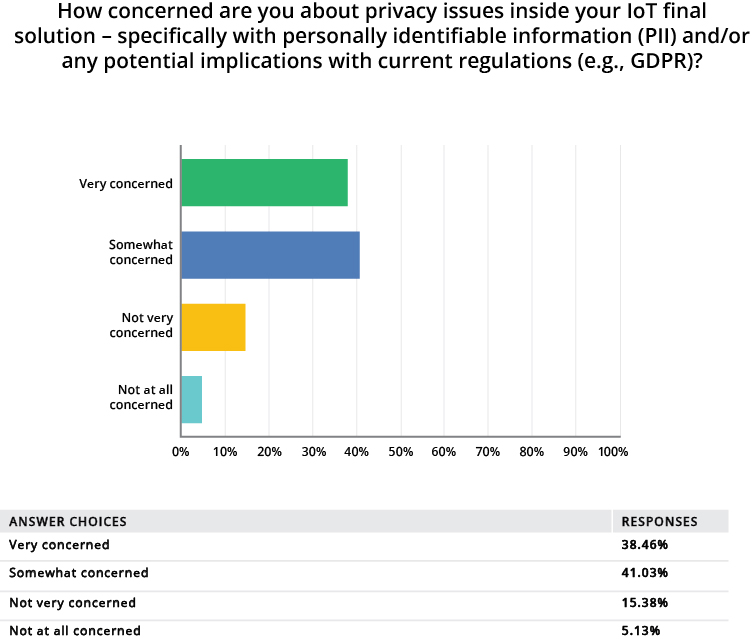
Figure 3: A majority of survey respondents stated that they felt “somewhat” or “very” concerned about privacy issues inside their IoT security solutions. (Source: GlobalSpec)
A majority of respondents also stated that they felt “somewhat” or “very” concerned about privacy issues inside their IoT security solutions. They expressed concerns about personally identifiable information (PII) and potential implications for current regulations such as the EU’s GDPR framework (see Figure 3).
While eye-opening, survey results like these are hardly surprising. IoT cybersecurity has a host of challenges, many of which derive from the organic, uneven evolution of the IoT itself.
(Source: N. Hanacek/NIST)
There is, for instance, no standard operating system or communication protocol for the billions of connected devices. Some devices may have security features built into their hardware at the chip level. Meanwhile, components of non-upgradable legacy systems may rely on inherently less secure software patches.
Device hardware resources can also limit security. These tend to be characterized by lower computing power, battery power and storage capacity compared to more traditional, nonconnected analogs.
Another challenge is that IoT devices are typically designed to be long-lasting and deployed in large numbers, often across wide areas. Therefore, they are more vulnerable to physical access and compromise over longer periods.
Meeting the Cybersecurity Challenge
As Telit Cinterion sees it, the key to meeting the IoT cybersecurity challenge is to take a proactive (as opposed to reactive) stance. Being proactive requires the kind of multilayer, 360-degree system view that the rapid evolution of the IoT lacked.
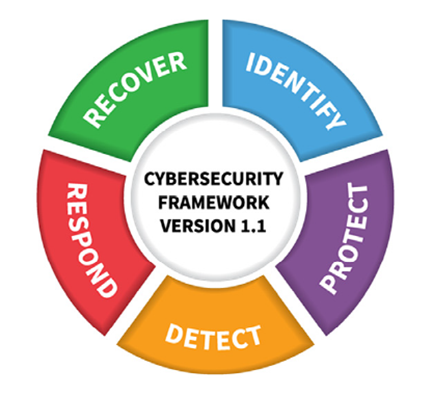
Guidelines such as ISO/ISE 27001 underscore the value of this type of organized approach. In addition, the cybersecurity framework (CSF) developed by the National Institute of Standards and Technology (NIST), part of the U.S. Department of Commerce, emphasizes its importance.
The NIST CSF Quick Start Guide, for example, identifies five key functions intended to encompass the full life cycle
of managing cybersecurity (see Figure 4). Organizations can manage and reduce their risk exposure by performing
activities within each key function, including:
- Threat, vulnerability and asset risk identification
- Encryption and integrity checks to protect sensitive data
- Log maintenance and monitoring to detect expected network behavior anomalies
- Response plan testing
- Regular recovery plan updates, incorporating lessons learned from past cybersecurity events
While the NIST CSF can be an excellent starting point for organizations, full implementation may require investment
in additional staffing and computing resources. More important than selecting a specific framework is the ability to
implement it.
Focused Approach to IoT Cybersecurity
Telit Cinterion’s IoT cybersecurity approach draws upon its digital identity expertise in establishing design rules for both hardware and software. These rules enable the creation of a unique identity for each IoT device, similar to personal identity documents (e.g., ID cards and passports). Identities are stored in device hardware. From there, they can be used to recognize devices interacting with the cloud to ensure security has not been compromised.
A crucial feature of Telit Cinterion’s approach is its focus on the system’s deepest level: the modules embedded within IoT devices. These can also be viewed as the IoT’s most vulnerable aspect, as any compromised module exposes the entire system and puts it at risk. Assigning permanent, unique identities to each module enables various secure activities, including:
- Zero-touch device onboarding
- Remote management
- Secure cloud platform synchronization
- Secure network transport
In the GlobalSpec survey, the highest-scoring answers about top cybersecurity concerns when choosing an IoT module (see Figure 5) revealed the importance of:
- Support for security upgrade capabilities
- New security feature costs
- The ability to integrate module security features
Each concern is addressed by Telit Cinterion’s module-focused approach, which includes:
- Advanced tools for device management and software updates
- Firmware and application signing to prevent execution of unauthorized or malicious code
- Several security feature specifications selected as most important by survey respondents (e.g., trusted device identity and data storage encryption) contained within Telit Cinterion’s most basic offering
- Local interface protection to prevent disclosure of sensitive information, tampering and reverse engineering
- Cryptographic APIs and security features are provided as part of module SDKs, supporting developers and easing integration into customer applications

Figure 5: Telit Cinterion takes an end-to-end approach to IoT system security. Source: (Telit Cinterion)
Another important aspect of Telit Cinterion’s approach is its end-to-end nature. It addresses the three-part structure of a typical IoT system: devices, infrastructure and cloud (see Figure 5).
Most GlobalSpec survey respondents viewed security concerns at each system level as equally important, highlighting the value of end-to-end system solutions.
Moreover, the company complies with ISO/ISE 27001. This indicates that Telit Cinterion meets the International
Organization for Standardization (ISO) criteria for a secure and well-run business.
Location Matters
Another concern highlighted by the GlobalSpec survey is the module and chipset manufacturers’ location. This factor can influence supply chain integrity and, considering the risks of cybercrime vulnerability, even impact national security. Nearly 80% of respondents indicated that manufacturer location “somewhat matters” or “matters very much,” compared to 5% who said it didn’t matter (see Figure 6).
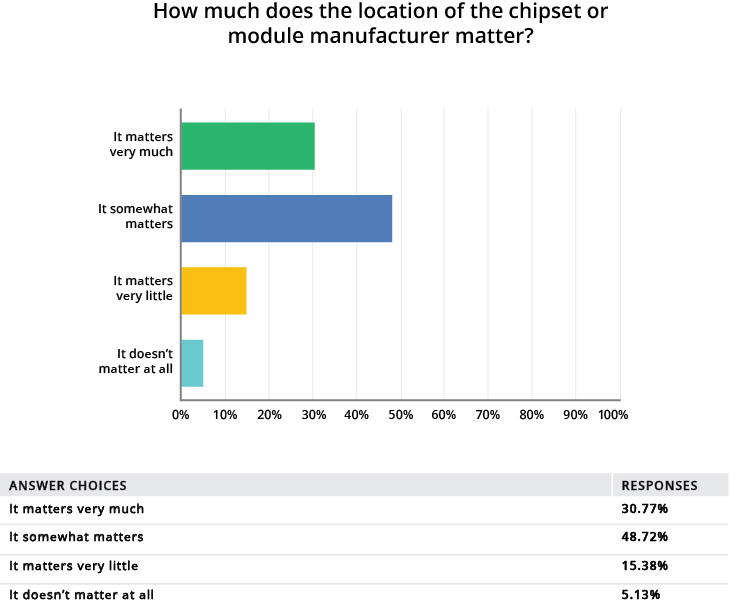
Figure 6: Nearly 80% of survey respondents indicated that manufacturer location “somewhat matters” or “matters very much,” compared to 5% who said it didn’t matter. (Source: GlobalSpec)
Similar questions about IoT connectivity were also important to survey respondents. They wanted to know the country where the mobile network operator (MNO) or mobile virtual network operator (MVNO) is headquartered. Telit Cinterion’s commitment to maintaining a Western focus in terms of production and utilized technology is a fit for many IoT stakeholders.
Beyond Partnership
The insights gleaned from the GlobalSpec survey align with Telit Cinterion’s:
- Modular focus
- End-to-end approach
- Western-oriented commitment
This alignment indicates that Telit Cinterion has its finger on the pulse of what’s most critical in ensuring security as IoT evolves.
Telit Cinterion builds turnkey, ready-to-launch IoT solutions for security integration with its modules, connectivity plans and services and platforms. It offers one source for all operations and infrastructure components. Telit Cinterion also aims beyond the trusted partner role. It has positioned itself as a trusted advisor that can offer tailored guidance and build custom solutions.
Request a consultation with a Telit Cinterion IoT expert to learn more about its secure IoT modules, connectivity, solutions and platforms.
Key Takeaways
- The GlobalSpec survey reveals IoT cybersecurity concerns surrounding module security and connectivity. Almost 80% of respondents said that a module manufacturer’s location “somewhat matters” or “matters very much.”
- The NIST cybersecurity framework provides guidelines and best practices for managing cybersecurity across an IoT system’s life cycle.
- Telit Cinterion’s IoT security solutions focus on enabling secure communication and data encryption and offering end-to-end system integration and support.


