Estimated reading time: 21 minutes

Fleet telematics enables businesses to remotely monitor and control a fleet. It makes insights into real-time vehicle data possible (e.g., gas mileage and vehicle diagnostics).
The Internet of Things (IoT) broadens the scope for monitoring and controlling large machinery and its subsystems. However, it does not come without security risks.
with IoT
Tracking and controlling fleets of large pieces of equipment is a critical IoT application. Data outages and breaches cannot be tolerated because of the risks. These can range from a simple late delivery to operator harm.
Security must be woven into the entire IoT system’s fabric, from the edge to the enterprise. Security by design provides insights into data and its movement to address evolving threats in the IoT landscape.
This e-book highlights:
- The security by design approach for IoT systems
- How it prevents hacking within the fleet management application
- How Telit Cinterion ensures top security in fleet telematics with a platform-agnostic device management system that prioritizes security
Table of Contents
What Is Telematics?
Telematics delivers real-time information by blending:
- Information technology (IT)
- Wireless networks such as cellular (e.g., LTE-M, 4G LTE and 5G)
- Wi-Fi and satellite (e.g., GNSS and non-terrestrial networks)
- Other IoT communication protocols (e.g., Bluetooth® wireless technology)
This data is transmitted from vehicles and analyzed. The server can send commands or new operational parameters to the mobile device or vehicle. The embedded application itself can also be updated. The vehicles have sensors and IoT modules for wireless connectivity to send and receive data for analysis.
What Are Telematics Systems Used For?
Telematics is used for asset tracking and fleet vehicle management to optimize routes, control fuel costs and remotely diagnose vehicle maintenance requirements.
Remote Diagnostics
Real-time fleet telematics gives information on a vehicle’s systems while driving, using remote diagnostics for insights. Leveraging this data increases productivity and reduces expenses. This data can be used to predict and prevent issues, reducing costs by fixing problems before they occur.
Route Optimization
Route optimization for deliveries is highly desirable. Last-mile delivery currently represents 53% of a company’s total delivery cost. It is expected to experience 78% growth through 2030.
Gaining a better understanding of real-time traffic and vehicle data ensures that vehicles can take optimal delivery routes. These optimized routes enable companies to reduce fuel costs, enhance fleet usage and improve fleet security.
Route optimization is especially relevant for applications that require accurate delivery times (e.g., cold supply chains).
Asset Tracking
Real-time vehicle location tracking allows for better fleet control and increases on-time arrival certainty. Asset tracking solutions are critical for time-sensitive cargo like pharmaceuticals or fresh produce.
Increased supply chain visibility helps users to determine who is responsible for cargo during transport. This makes sending insurance claims to the right person easier and reduces transportation risks.
Asset tracking also enables more accurate billing based on usage specifics. For example, cement mixing trucks are precisely timed when water is added to the batch and the mixing begins. The concrete is ready to be used once the mixture has undergone enough drum revolutions.
Ideally, there would be no wait from when the batch is ready to when it is poured. However, these trucks are often forced to wait lengthy periods before delivering the product to worksites. Vehicle tracking monitors the precise time lost and any required corresponding billing, allowing for higher operational cost accuracy.
Cross-checking cargo location data with its condition enables businesses to understand where goods were damaged in the supply chain.
Fleet Applications and the Importance of Telematics
A study from the United States Census Bureau in 2021 showed that trucks transported 71.6% ($10.4 trillion) of the value of all goods shipped within the U.S. ($14.5 trillion). Europe’s road freight market was over €300 billion in 2020.

These goods include:
- Base metal
- Plastic and rubber materials for manufacturing
- Gasoline
- Electronics
- Motorized vehicles
Cold chain perishable goods also account for an enormous portion of transported goods. This industry relies on an unimpeded flow of trucks and is crucial to a nation’s economy and prosperity.
Disruptions can cause major industries to shut down. It can also prevent vital emergency goods from reaching areas hit by natural disasters, Hurricane Katrina being an example. Trucks were rerouted, causing major delays to affected areas needing supplies.
This flow can also be impacted by border restrictions based on the decisions of public officials. Several major auto manufacturing plants were affected by shutdowns and delays at the U.S. and Canadian border after 9/11.
The same happened with Brexit border regulations for the Eurotunnel’s Calais terminal. These events disrupted the supply chain as just-in-time parts were not delivered.
Telematics also assists with usage-based insurance (UBI) for pay-as-you-drive (PAYD) and pay-how-you-drive (PHYD) systems. Measurements taken while driving the vehicle contribute to driver-specific data that optimizes insurance rates.
Telematics applications for fleet management are not limited to trucks. Expensive fleets like heavy equipment for mining, construction and agriculture must be monitored for maintenance and smooth operations.
Transporting shipping containers is a risky process. Cargo is subjected to handling, inspection and transport that typically go unmonitored. Therefore, it is often damaged or lost without a known cause.
In December 2022, the Transported Asset Protection Association (TAPA) recorded an average of 20 daily cargo theft incidents across Europe, the Middle East and Africa. In one month, it totaled losses of more than €17 million — over $18 million. Mislaid or mislabeled containers or unauthorized access to containers in a fleet can be easily identified with the right fleet management solution.
The Large Attack Surface of IoT Systems
Vulnerability on the Rise
The rise of IoT devices has increased the attack surface, making it a tempting cyberattack target. With a continued annual growth rate of 12.57%, the market volume will increase to more than $2.2 trillion by 2028. The staggering number of attack opportunities makes IoT a highly desirable business opportunity. However, it also creates a larger target for bad actors.
Every IoT device — from smartphones to home security systems — is susceptible to cybersecurity risks. Over half of these devices were vulnerable to medium- to high-level attacks.
Cyberattacks on IoT infrastructure have grown exponentially in the last few years. The first half of 2021 saw 1.5 billion IoT cyber incidents reported ― a number projected to continue growing.
This dynamic problem requires businesses to stay apprised of all devices and data movements. New attacks have occurred in as little as five minutes after a device is connected to the internet. Other attacks can also succeed as quickly as 15 minutes after publishing common vulnerabilities and exposures (CVE) lists. Vulnerabilities with a high enough common vulnerability scoring system (CVSS) score can cause catastrophic results.
This could be seen, for example, in the Apache Log4j critical vulnerability (CVSS score of 10) found in late November 2021. Log4j allowed attackers to drop malware on a target system, compromising the network and leading to the theft of sensitive information.
This logging utility has been downloaded millions of times and is in thousands, if not millions, of field devices. After the CVE was published, cybersecurity researchers logged millions of attempts to use it in attacks, which has increased to 10 million attempts per hour. On January 4, 2022, the FTC threatened companies with fines if they did not resolve the CV ― a little over a month after the initial vulnerability was discovered.
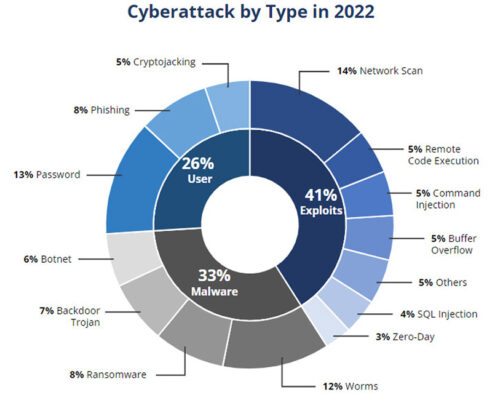
Companies must consider the number and severity of security vulnerabilities and patches for them. In addition, they must also consider fines and damage to the company’s reputation. Figure 2 shows a breakdown of cyberattack types found in 2022. As shown, there is an even distribution between user vulnerabilities, malware and exploits.
The Risks Associated with Telematics Systems
Telematics system vulnerabilities can come with business- or even life-threatening consequences. Telematics boxes used for fleet management can involve some of the worst-case scenarios in which entire fleets can be controlled.
Vulnerabilities in safety-critical features (e.g., steering and acceleration) pose serious risks to the operator and others around them. This problem is multiplied by thousands of fleets in different geographic locations. Fleet equipment replacement costs are thousands to millions of dollars per vehicle. Therefore, equipment damage is also an unacceptable risk.
Security features like unlocking and starting a vehicle can be turned off until a ransom is paid (also known as file locking blackmail). This attack could shut down shipment operations, wreaking havoc on the supply chain and risking critical asset delivery.
Maintaining information fidelity for remote monitoring and diagnostics requires a real-time data feed for smooth supply chain operations. This data must not be manipulated or altered.
Location surveillance is another risk. It is possible to run a global surveillance network on fleet vehicle locations. Such intelligence data can be valuable to hijackers (e.g., locations of armored car carriers or high-value commercial fleets). The insurance black box or OBD dongles pose as attack vectors to penetrate the vehicle itself or back-end servers to steal valuable data.
Real-World Examples of Attacks on Fleet Telematics Systems
An example of an insurance black box hack can be seen in the vulnerability exposed in 2015. Researchers hacked into a connected OBD-II to remotely enable Corvette’s wipers and engage and turn off brakes at low speed. While this was done to a commercial car and not a fleet vehicle, it exposes a vulnerability in telematics.

In 2019, another hacker broke into iTrack and ProTrack GPS tracking apps. Companies often used these apps to monitor and manage fleets. The hacker gained access to monitor the vehicles’ locations and even turn off engines while some vehicles were in motion. He claimed he could “control hundreds of thousands of vehicles” and “by one touch” stop their engines.

Altering a vehicle’s odometer is another hacking method used in fleet vehicles to change vehicle mileage and rip off buyers. According to the National Highway Traffic Safety Administration (NHTSA), more than 450,000 vehicles are sold yearly with false odometer readings. This problem costs American consumers an average of $1 billion annually.
Many of these cybersecurity risks have catastrophic consequences that cannot be taken lightly. These susceptibilities can make operating large fleets of vehicles a serious threat on the road. For this reason, building security into the entire IoT chain is prudent, from the embedded systems to the enterprise system. In addition, routine security assessments should be performed to fend off attacks.
The Security by Design Approach for IoT
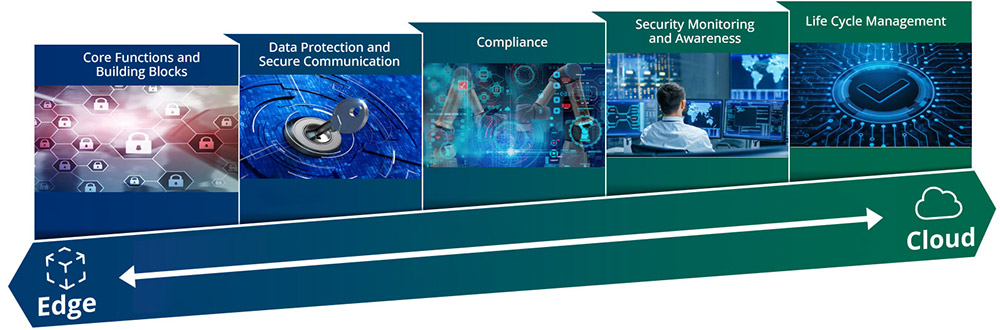
Figure 3 shows that every IoT solution is a complex structure in which information flows through many layers from the edge to the core of the business. Creating a secure IoT solution requires breaking down these functions and identifying transition points. This strategy establishes a series of security measures that reflect how the IoT system operates.
Security is not wrapped around a solution like a blanket. It is more like the thread that is woven into the fabric of the solution itself. The solution must be viewed holistically. Care must be taken to ensure that secure components are introduced and assembled where each connection, transition and integration point is secured.
For instance, the National Motor Freight Traffic Association (NMFTA) requires that “monitoring of the entire fleet or subsets thereof is made possible by dashboard or operations center features” for telematics cybersecurity.
This approach allows companies to create tailored solutions to overcome evolving security threats inherent to the hyperconnected world. There are two steps within this process:
- Create a catalog of IoT assets and the critical functions across the chain.
- Develop security strategies identified in the risk management process for each layer.
The security approach for one IoT solution may not be suitable for another. The level of risk also varies within IoT.
For example, the risks associated with smart lighting differ from industrial automation, medical and public safety IoT applications. This consideration is fundamental for security by design. It will determine the security, redundancy and compliance level required within these systems.
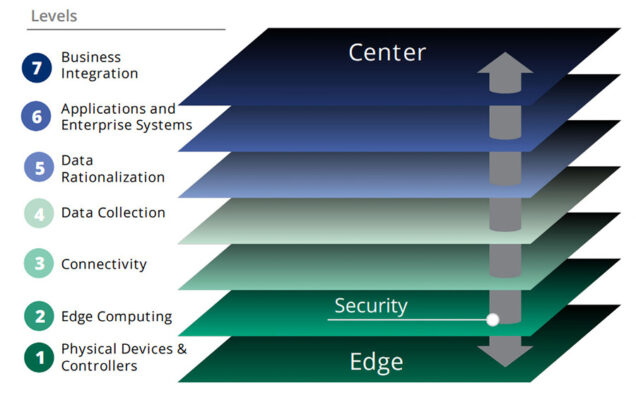
The Structure of the IoT Chain
The IoT structure begins with physical devices (e.g., sensors, actuators and controllers) that monitor and control objects, such as fleet vehicles or robotic arms. Then, the device can collect and analyze data from the sensors locally so the system may take actions in the physical world through actuators.
This is commonly the case in edge computing applications, in which some of the computing burden is moved closer to the edge. This cuts out much of the round-trip latency on data sent to and from the edge device with cloud computing. In addition, it increases the autonomy of the IoT solution. However, edge intelligence is not used for all IoT applications.
All IoT applications are wirelessly connected to the cloud through some type of network connectivity. Many utilize public ISM bands, such as:
- Wi-Fi
- Bluetooth wireless technology
- LoRaWAN
- Sigfox
- Zigbee
- Thread
Others use licensed bands such as cellular solutions (e.g., 4G LTE, 5G, LPWA). Data must be securely and efficiently collected from the edge and rationalized for integration into the enterprise IT systems.
Data rationalization enables complex data sets to be reduced and prepared to extract value for better insight and to guide business operations and decisions. This can be seen in fleet telematics, in which all supply chain information can be viewed on a single pane of glass.
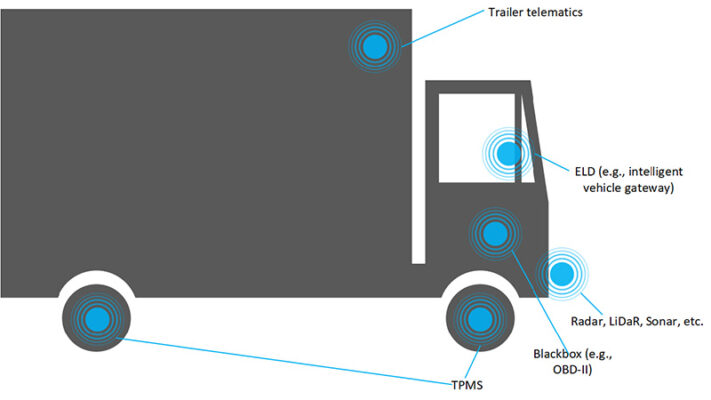
Centralizing this information empowers the business to cut costs and find areas within the organization to optimize operations. Smaller business decisions like predictive maintenance and finding faster routes based on traffic can easily happen with these systems.
Establishing Security by Design Measures in Fleet Management
As stated, the attack surface that cyberattackers can exploit grows with the number of IoT devices. To successfully weave security into the entire IoT design from the edge to the enterprise, assess where the vulnerabilities are to identify every attack vector.
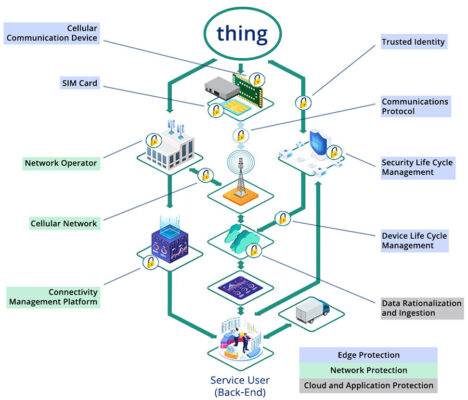
Figure 5 shows a fleet telematics IoT solution setup with several attack surfaces that could be exploited.
All sensors, actuators and control modules can be compromised during manufacturing (#1). This can happen, for example, by exposing secrets or building the wrong software. It is important to ensure that the code running on the device is always trusted and that all keys and credentials are securely stored (#2 and #4).
A fleet telematics solution must have tools and services to distribute the software and security patches (#5). In addition, they must monitor the device for any strange behavior indicative of an ongoing attack (#7 and #8). One security consideration is to control access to the device to avoid unauthorized users tampering with its settings (#3 and #6).
Managing digital identities is another key aspect of security by design (#9). Businesses must correctly implement the authentication and authorization layers to protect the data and restrict access to the services ecosystem (#10).
Operations should be managed according to the best practices and standard security frameworks (#11). Moreover, a robust connectivity management service must be implemented (#12). Finally, it is critical to securely manage access to functions that turn the device on or off at the start. This can disrupt service and even disconnect the device for good (#13).
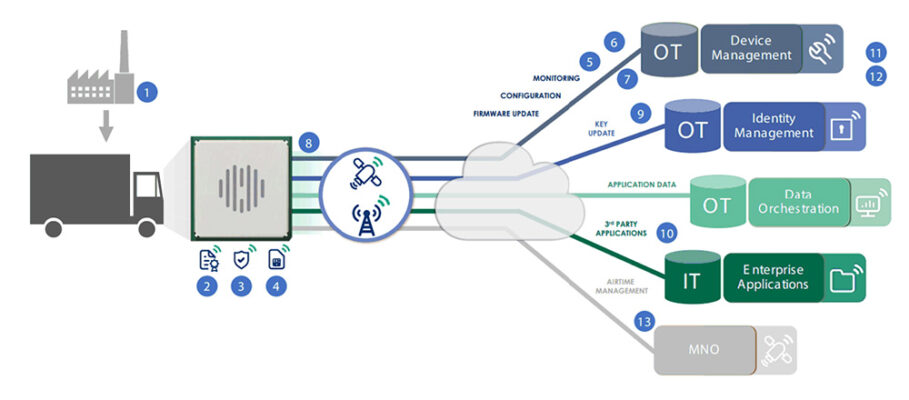
Security by Design from Edge to Enterprise
Edge Device Protection
Identification and Authentication
Threat remediation starts at the edge, where physical devices must establish the validity of official firmware images while being protected against rogue ones. These devices must be used with an identity to authenticate and onboard the services securely. This process is enabled during manufacturing to simplify operations and increase security.
Secure Firmware and Update Processes
Devices should cryptographically check the software before execution to avoid executing malicious software. Any updates or changes to the device firmware should be done securely and reliably without introducing vulnerabilities.
Secure Data Storage
Chips often have secure building blocks that allow users to store credentials and keys. If these features are available, it makes sense to take advantage of them. The SIM is a secure embedded Universal Integrated Circuit Card (eUICC) for cellular-enabled devices. It can be a secure trust zone for sensitive data and credentials.
Secure Communication Protocols
Communications must be encrypted using state-of-the-art cryptographic implementations. Confidentiality, integrity and availability are fundamental security aspects. They are achieved using a transport layer security (TLS) cyber suite that manages the asymmetric handshake, enabling asymmetric encryption.
Physical and Logical Interface Protection
Physical and logical interfaces must be secured by locking them, for example, when a device is deployed in the field. The backports must either be entirely turned off or have only authenticated access.
Device and Security Life Cycle Management
Life cycle management services are important to ensure the device is properly provisioned, monitored and maintained for its entire lifetime. This includes the device’s configuration, software and identity.
It is important to address newly discovered vulnerabilities and manage security credentials. The system managing security must also be protected. Middleware can improve IoT design efficiency and offer a closed connectivity security solution with mutual authentication.
Network Connectivity Protection
Robust connectivity management platforms (CMPs) offer features to address challenges associated with managing IoT devices and connections, including:
- Monitoring traffic and usage patterns
- Detecting outages and preventing distributed denial of service (DDoS) attacks
- Detecting unauthorized endpoints
- Addressing privacy concerns and data protection
Monitoring network traffic and usage helps prevent misuse of company data and ensures it remains secure. This includes ensuring that data is not sent to unauthorized locations, or external users are not accessing the company network.
For example, platforms capable of disabling SIM cards can cut off communications with any device that is interfered with and poses a threat. A private APN and VPN are also essential for confidentiality. These establish a secure, private network for devices to address privacy concerns and data protection.
CMPs can help detect outages and DDoS attacks early so the company can take appropriate action to mitigate the impact. Outages are also an unacceptable risk to critical devices. A backup network profile ensures guaranteed connectivity.
Data and application protection relies on several security attributes, including:
- A trusted cloud provider
- Secure endpoints provisioning
- Identity and access management
- Encrypted communications links
- Third-party data integration
- Logging and monitoring
Data and Applications Protection with Security by Design
Using a trusted cloud provider to protect data and applications is important. Secure end-device provisioning to a third-party cloud ensures that all devices connecting to an application or cloud service are provisioned securely.
Devices must be securely ingested into public clouds. A device management platform can load the device’s identity into the cloud independently of the data channel.
Identity and access management is another important aspect of application-level security. It involves controlling access to assets and data, ensuring only authorized users or authorized applications can use critical information. Encrypted communication links protect the data transmitted between devices and applications from interception and tampering.
Service and data integration for third-party services cannot be overlooked. Third-party services and APIs used by the applications must not introduce vulnerabilities. Logging and monitoring all activities is crucial to detect situations that could indicate a security breach or other issue.
Compliance

Finally, adopting international cybersecurity frameworks for operations and processes is another way to achieve security. These frameworks provide requirements on how to identify vulnerabilities and risks.
Business continuity management and resiliency plans that follow guidelines ensure that all applications and data are accessible even during disasters or disruptions. Part of this is continuous monitoring and proactive assessment. Security is a dynamic operation that anticipates issues and resolves them as they appear.
Security by Design: Fleet Management Security Measures
Easy Viewing of Data across All Vehicles
Fleet management is undoubtedly vital to the movement of goods. Most shipments made within the U.S. are accomplished using trucks. Trucks carry 77% of all freight transported over land in the EU. More than 6.2 million trucks are circulated throughout the EU, and 13.5 million are registered in the U.S.
Fleet management requires a deep understanding of the data patterns and flow between the fleet and back-end computer system. Viewing operations across multiple systems and locations from a single pane of glass is important to accomplish this. This consolidated view reduces the number of systems that must be maintained. Moreover, it automates non-essential or non-safety-critical tasks, freeing up time for more high-value use cases.

Telit Cinterion’s device management and cellular connectivity plans and services do this with the IoT Portal for comprehensive global IoT deployment control. It offers modules with embedded GNSS positioning technologies. In addition, Telit Cinterion’s cellular IoT modules provide data, SMS and voice on Tier 1 networks worldwide. These capabilities are ideal for fleet management solutions as communication with moving trucks is required.
Moreover, NExT™ embedded connectivity, powered by Telit Cinterion, is an embedded SIM (eSIM) solution. It offers device-server data transmission that provides worldwide coverage by securely and remotely switching providers as needed. Only one SIM is necessary for the device’s entire life cycle. Users can switch carriers or technologies without swapping SIMs on-site.
Incorporating the Security by Design Approach for Fleet Telematics
In the U.S., the Department of Homeland Security and the Department of Transportation’s Volpe Center released a “Telematics Cybersecurity Primer for Agencies” in 2017. It addressed the concerns about protecting fleet management data, systems and assets.
Protecting the fleet management information system (FMIS) or electronic logging device tools boils down to protecting:
- Communications within the FMIS via encryption and authentication
- The FMIS via software and firmware protocols like digital signatures or encryption
- FMIS actions via the use of minimal rights and enabling of minimal services
- The integrity of the FMIS via authentication, vulnerability management and penetration testing
These features are integrated into Telit Cinterion’s security by design approach. Moreover, this method is found within the company’s robust cellular connectivity solutions, including hardware, connectivity and platforms. The solutions are platform-agnostic and can be integrated with deviceWISE®, powered by Telit Cinterion. They can also integrate with a third-party platform to create a secure fleet telematics solution.
The services are based on reliable and secure software as a service (SaaS) infrastructure with edge device and network connectivity protections. These include a strong authentication mechanism, authorization, zero-touch provisioning and SSO integration. Cloud and application security aspects and compliance are enhanced with:
- Secure API integration for third parties
- Seamless integration with hyperscalers like AWS and Microsoft Azure
- Security analytics
- ISO 27001 certified operations
- Georedundancy and geofencing alerts
Summary

Cybersecurity in fleet telematics is paramount to ensure the safety of company data (e.g., fleet locations and diagnostic information) and the operators. The risks require a security by design approach, which considers security at every stage of the telematics IoT chain.
Telit Cinterion has been in this market for over 30 years with a range of solutions spanning the full IoT value chain. It offers a portfolio of wireless modules, connectivity services and platforms to simplify design, deployment and device life cycle management.
The company’s experience gives it a unique position to understand the challenges with the telematics IoT ecosystem. Businesses can onboard devices to hyperscaler clouds securely.
Telit Cinterion offers a range of hardware and software products for the most complex telematics needs. Speak with Telit Cinterion’s experts to learn more about security by design and discover the possibilities of a secure fleet telematics system.
Key Takeaways
- The security by design approach for fleet telematics applications addresses vulnerabilities proactively, safeguarding data and mitigating cyberattacks.
- Fleet telematics systems enable real-time vehicle monitoring and management. They offer capabilities like remote diagnostics and asset tracking to enhance and secure operations and reduce costs.
- The number of IoT devices is increasing, expanding the attack surface and making systems more susceptible to cyberattacks. Security measures like secure communication protocols and data encryption are vital to safeguard fleet telematics applications from hackers and breaches.


