Ripple20: What You Need to Know
By Mihai Voicu
August 27, 2020
Ripple20 is a cybersecurity threat so named because of the capacity for a ripple effect on the supply chain. Its vulnerabilities have been integrated into potentially billions of consumer, enterprise and industrial IoT devices over the last two decades.
Security expert firm JSOF stated that devices from many OEMs and integrators, including companies in medical, enterprise, telecom, energy, retail and other verticals, are vulnerable. Cybercriminals can exploit the weakness to steal data or cause equipment to malfunction.
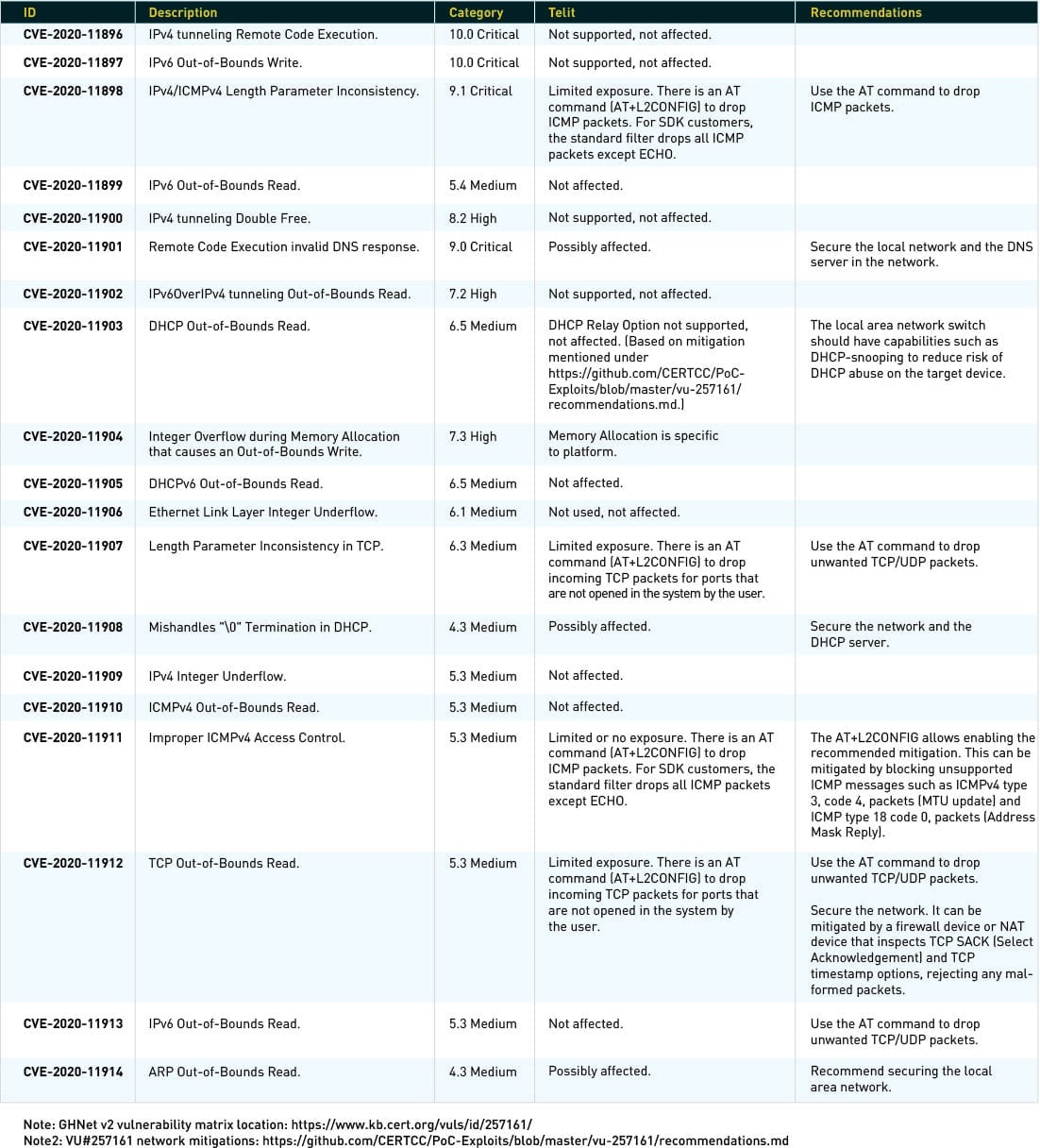
On 16 June 2020, JSOF’s research lab released a comprehensive report (called Ripple20) that outlines 19 vulnerabilities traced to certain versions of the TCP/IP stack from Treck Inc.
More details can be found at:
https://www.us-cert.gov/ics/advisories/icsa-20-168-01
https://treck.com/vulnerability-response-information/ 
Vulnerabilities have been listed in the CVE database with the following numbers:
The research report (https://www.jsof-tech.com/ripple20/) shows Telit as a possible vendor using libraries from Treck Inc.
Since the news broke in May 2020, Telit has been working with Treck Inc., CISA and ISC-CERT to understand the impact of the vulnerabilities on Telit products.
As of today, our investigation has only found that Treck Inc. TCP/IP stack libraries have been used in the following products: GS1011 and GS1500. These products have been EOL since 2017.
We’ll be monitoring the situation as it develops. Please see below for updates.
For any other details, please contact our security team.
The GS1011 and GS1500 products use Green Hills Software LLC’s GHnet™ v2 network stack, which is based on Treck Inc.’s network stack. However, GHnet v2 and Treck’s network stack are not identical. Green Hills Software has made many improvements, added new features and fixed bugs in the product, making the vulnerabilities’ impact far less severe.
Telit (formerly GainSpan) has made further adaptations in its platform and removed many unnecessary features. The stack doesn’t support IPv4 tunneling, IP routing, IP fragmentation and IPv6. Therefore, most of the vulnerabilities affecting those are not applicable, limiting the exposure.
The platform is usually deployed in ultralow-power mode. In this mode, the device is sleeping most of the time, sending data at fixed intervals and receiving only on an as-needed basis. Also, filtering the undesired packets at the lowest levels before they’re passed to the stacks allows only packets for open, user-enabled ports, making the attacks less likely.
We recommend securing the local area networks to ensure there are no unexpected packets.
Last updated: 27 August 2020 at 9:00 a.m.