Next-Generation IoT Security Architecture
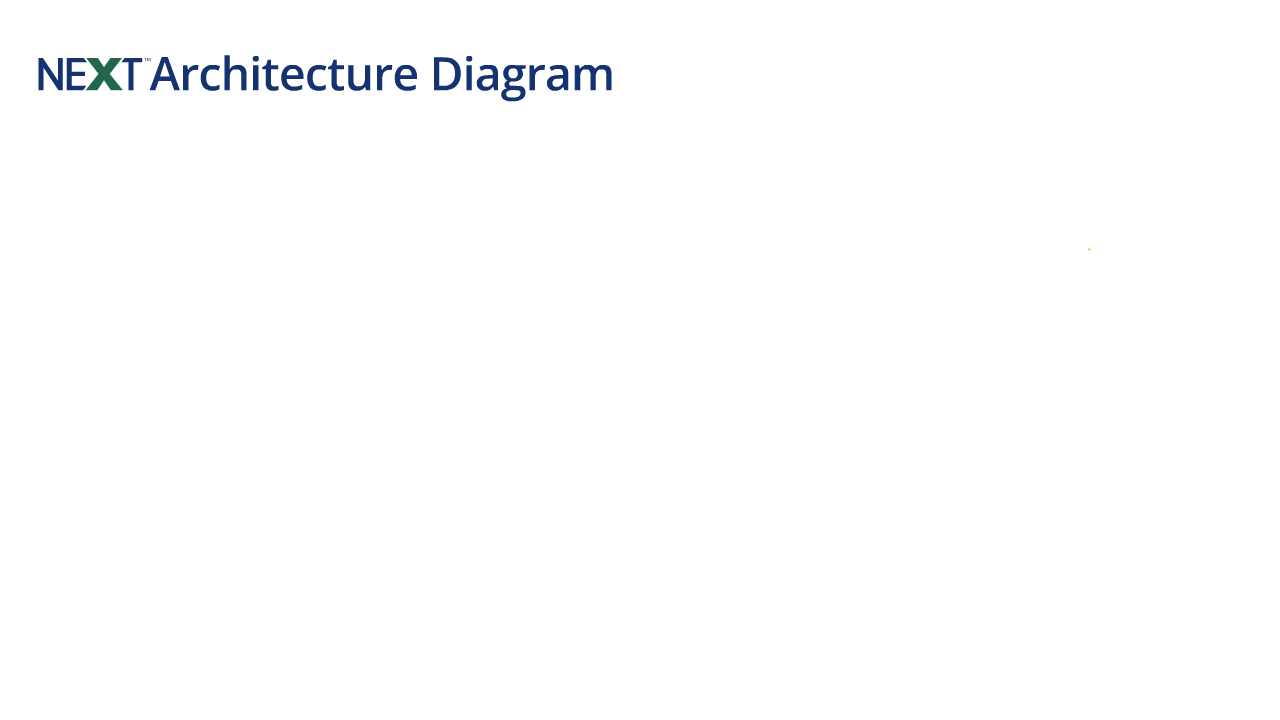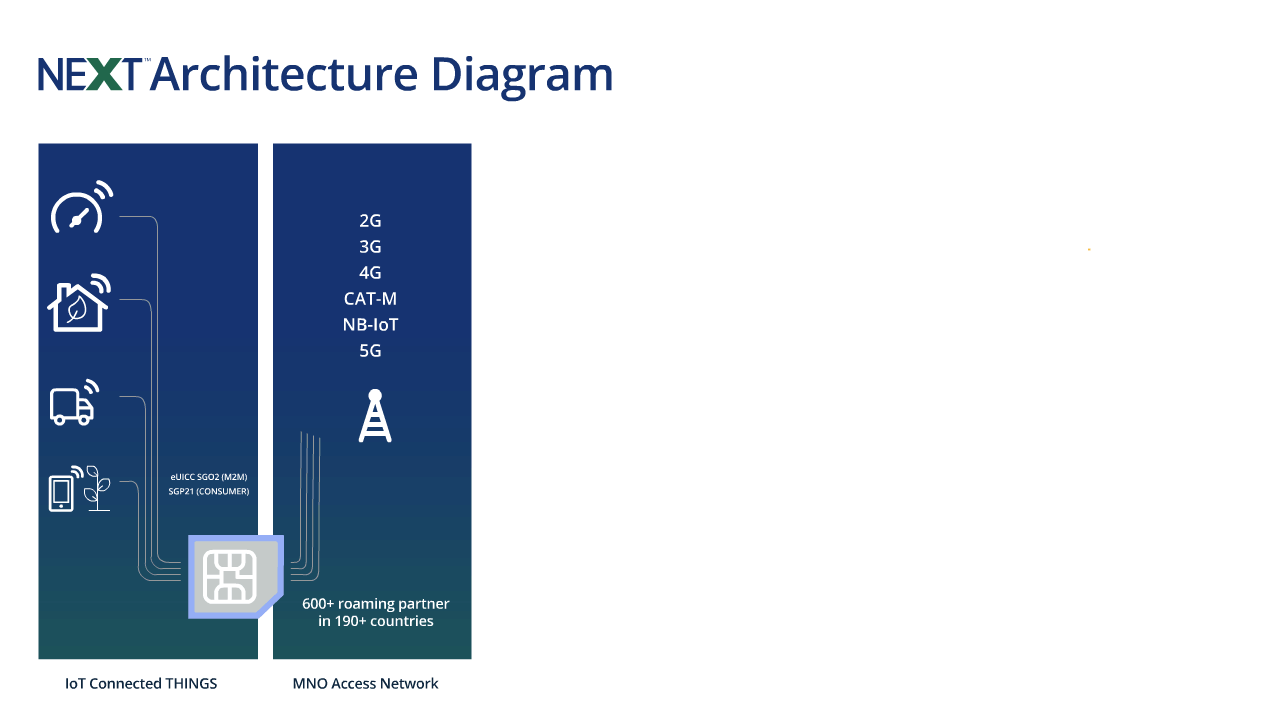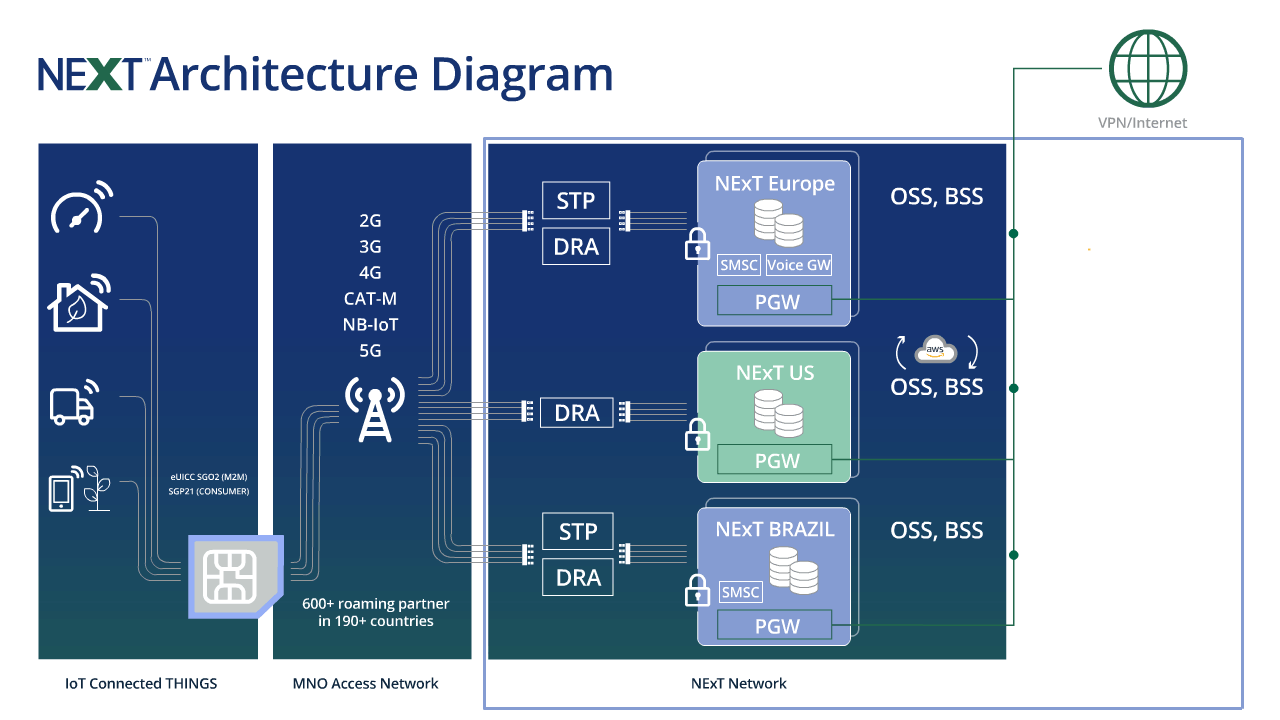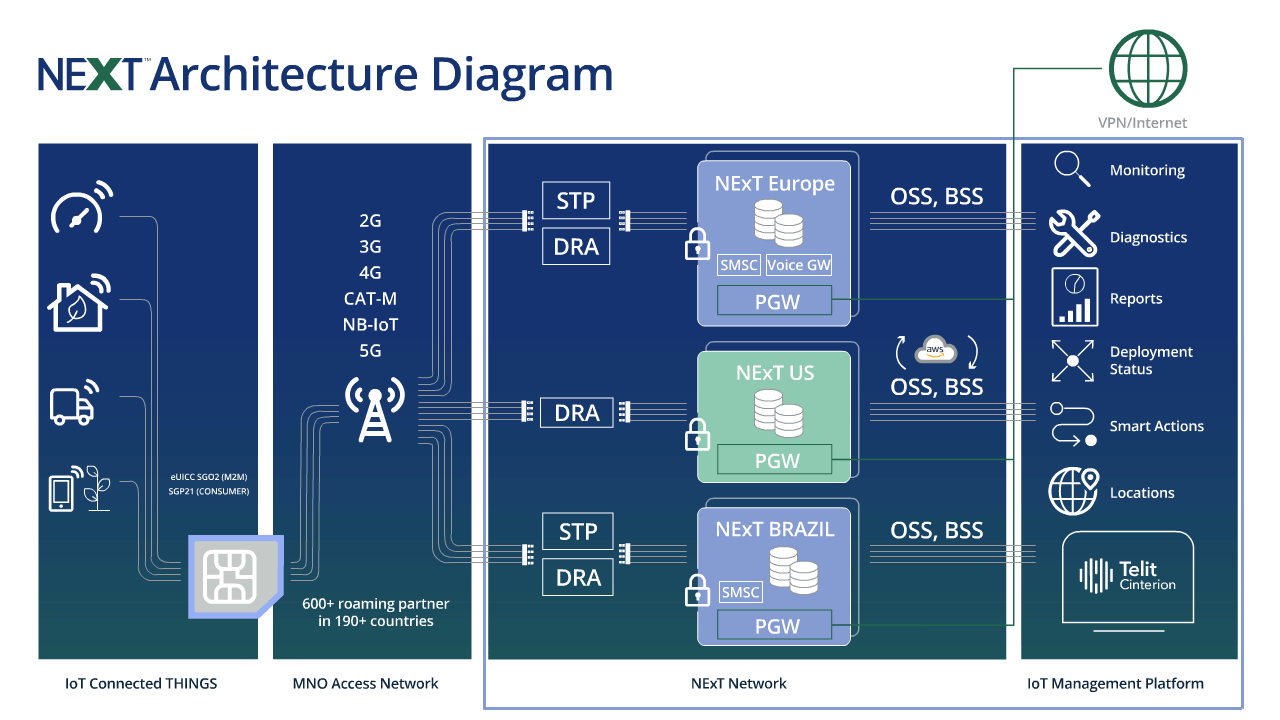
The NExT™ IoT core network, powered by Telit Cinterion, delivers advanced security and cloud-native architecture. It facilitates secure onboarding across more than 600 carriers in over 200 countries.
With multi-IMSI and eUICC, this network supports scalable enterprise deployments. No matter the use case, NExT ensures resilient connectivity backed by Telit Cinterion’s trusted infrastructure.